1. Introduction
Hello! We are a writer team from Definer Inc.
In this issue, you are wondering about the use of AWS Site-to-Site VPN components.
Let's take a look at the actual screens and resources to explain in detail.
2. Purpose/Use Case
This article introduces the AWS Site-to-Site VPN technology for the purpose of multi-cloud and cloud-on-premise connectivity.
It is a collection of information and practices that can be helpful for IT professionals who want to understand the components of AWS Site-to-Site VPN.
Here are specific cases where using a VPN can be beneficial:
- Public Wi-Fi Security: When using public Wi-Fi networks in places like cafes, airports, hotels, or libraries, you expose your data to potential hackers or snoopers. VPNs encrypt your data, making it much harder for anyone to intercept and steal sensitive information, such as passwords, financial details, or personal data.
- Bypassing Geographic Restrictions: Some websites, streaming services, or online content may be restricted based on your geographical location. With a VPN, you can change your virtual location and access content that might otherwise be blocked in your country.
- Privacy and Anonymity: VPNs can help protect your online identity by hiding your real IP address and routing your traffic through their servers. This makes it more difficult for websites, advertisers, or even your internet service provider (ISP) to track your online activities.
- Torrenting and P2P File Sharing: While torrenting and peer-to-peer file sharing can be legal in some cases, it can also expose your IP address to other users, leaving you vulnerable to potential legal issues or attacks. A VPN masks your IP address during these activities, enhancing your privacy.
- Business Use: Companies often use VPNs to allow remote employees to securely access internal networks and resources. This ensures that sensitive company data remains protected while being accessed from outside the office environment.
- Circumventing Censorship and Surveillance: In countries with strict internet censorship or heavy surveillance, VPNs can help bypass such restrictions and provide users with a way to access uncensored information and communicate privately.
- Secure Communication: VPNs can be useful for securing communications, especially when transmitting sensitive information between two parties, such as in business negotiations or confidential client communications.
- Avoiding Bandwidth Throttling: Some ISPs may intentionally slow down your internet connection when they detect certain online activities (e.g., streaming). Using a VPN can prevent or minimize such bandwidth throttling since your ISP won't be able to see what you are doing.
3. What is AWS Site-to-Site VPN?
AWS Site-to-Site VPN is a service that provides secure PVN connectivity between AWS and on-premise/other clouds.
AWS Site-to-Site VPN provides a VPN tunnel between a virtual private gateway or transit gateway on the AWS side and a customer gateway (VPN device) on the remote (on-premise/other cloud) side.
AWS Site-to-Site VPN supports Internet Protocol Security (IPsec) VPN connections.
AWS Site-to-Site VPN connections exist in either AWS VPN or AWS Classic VPN options.
All new AWS Site-to-Site VPN connections that are created are the former AWS VPN connections.
The following are some of the advantages of AWS VPN connections compared to AWS Classic VPN.
・IKEv2 (Internet Key Exchange version 2) is supported
AWS VPN supports IKEv2, an advanced encryption protocol used to establish secure communication channels between VPN devices. IKEv2 provides enhanced security and faster connection establishment compared to older protocols like IKEv1.
・Can be monitored by CloudWatch metrics
AWS VPN connections can be monitored using CloudWatch Metrics. Amazon CloudWatch allows you to collect and track various performance metrics related to your VPN connections, such as data transfer rates, latency, and connection status.
・Custom encryption options (AES 256, SHA-2 hash, etc.)
You can choose to use AES 256 (Advanced Encryption Standard with a 256-bit key) to secure your data during transit. Additionally, you can specify the use of SHA-2 (Secure Hash Algorithm 2) for integrity validation of the transmitted data.
・Custom tunneling options
AWS VPN connections allow you to configure custom tunneling options. Tunneling refers to the process of encapsulating data packets within another packet for secure transmission between VPN endpoints. With custom tunneling, you have more flexibility to define the tunneling protocols and parameters that best suit your specific networking requirements and security policies.
・Support for IPv6 traffic at transit gateways
AWS VPN connections can handle IPv6 traffic when used with AWS Transit Gateway. AWS Transit Gateway is a highly scalable service that simplifies interconnecting multiple Amazon Virtual Private Clouds (VPCs) and on-premises networks. The support for IPv6 traffic allows you to embrace the newer internet protocol and accommodate IPv6-based networks seamlessly in your AWS environment.
4. Components of AWS Site-to-Site VPN
Next, we will introduce the components of AWS Site-to-Site VPN.
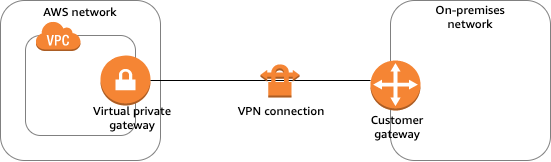
・Virtual Private Gateway
This is the VPN endpoint on the AWS side of the Site-to-Site VPN connection.
It acts as an entry and exit point for traffic between your VPC and your on-premises network. The VGW is associated with your VPC and facilitates communication between your VPC and the Customer Gateway (CGW) on your on-premises network.
(From AWS Site-to-Site VPN Structure)
 ・Transit Gateway
Transit Gateway is a VPN endpoint on the AWS side for Site-to-Site VPN connection.
It is a relay hub that can be attached to multiple VPCs (Virtual Private Cloud) and on-premises.
Site-to-Site VPN connection is created as a transit gateway attachment.
(From AWS Site-to-Site VPN Structure)
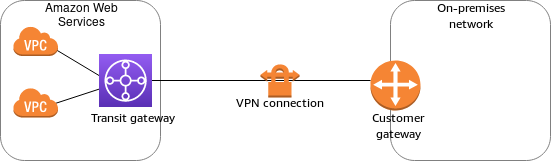
・Transit Gateway
Transit Gateway is a VPN endpoint on the AWS side for Site-to-Site VPN connection.
It is a relay hub that can be attached to multiple VPCs (Virtual Private Cloud) and on-premises.
Site-to-Site VPN connection is created as a transit gateway attachment.
(From AWS Site-to-Site VPN Structure)
 ・Customer Gateway
A physical device or software application on the user (remote) side.
Site-to-Site VPN connection requires network configuration for the Customer Gateway Knob Crane device or application on the remote network.
The CGW is responsible for establishing and managing the VPN connection from your on-premises network to the VGW in AWS. It must have a public IP address that is reachable over the internet.
In summary, create a virtual private gateway or transit gateway on the AWS side and a customer gateway on the remote side, and connect them to the VPN.
・Customer Gateway
A physical device or software application on the user (remote) side.
Site-to-Site VPN connection requires network configuration for the Customer Gateway Knob Crane device or application on the remote network.
The CGW is responsible for establishing and managing the VPN connection from your on-premises network to the VGW in AWS. It must have a public IP address that is reachable over the internet.
In summary, create a virtual private gateway or transit gateway on the AWS side and a customer gateway on the remote side, and connect them to the VPN.
 ・Transit Gateway
Transit Gateway is a VPN endpoint on the AWS side for Site-to-Site VPN connection.
It is a relay hub that can be attached to multiple VPCs (Virtual Private Cloud) and on-premises.
Site-to-Site VPN connection is created as a transit gateway attachment.
(From AWS Site-to-Site VPN Structure)
・Transit Gateway
Transit Gateway is a VPN endpoint on the AWS side for Site-to-Site VPN connection.
It is a relay hub that can be attached to multiple VPCs (Virtual Private Cloud) and on-premises.
Site-to-Site VPN connection is created as a transit gateway attachment.
(From AWS Site-to-Site VPN Structure)
 ・Customer Gateway
A physical device or software application on the user (remote) side.
Site-to-Site VPN connection requires network configuration for the Customer Gateway Knob Crane device or application on the remote network.
The CGW is responsible for establishing and managing the VPN connection from your on-premises network to the VGW in AWS. It must have a public IP address that is reachable over the internet.
In summary, create a virtual private gateway or transit gateway on the AWS side and a customer gateway on the remote side, and connect them to the VPN.
・Customer Gateway
A physical device or software application on the user (remote) side.
Site-to-Site VPN connection requires network configuration for the Customer Gateway Knob Crane device or application on the remote network.
The CGW is responsible for establishing and managing the VPN connection from your on-premises network to the VGW in AWS. It must have a public IP address that is reachable over the internet.
In summary, create a virtual private gateway or transit gateway on the AWS side and a customer gateway on the remote side, and connect them to the VPN. 5. Getting started with AWS Client VPN
In this tutorial, we will set up a Client VPN with mutual authentication, which means both the clients and the Client VPN endpoint will use certificates for authentication. This adds an extra layer of security to our VPN connection.
Step 1: Prepare Certificates
You will need to have a server certificate and key, and at least one client certificate and key. You can use OpenVPN package to generate service and client certificates. Read more about OpenVPN-Easy-RSA in here.
After certificates generation, we have 5 files: certificate chain file, server cert file, server key file, client cert file and client key file.
The server certificate must be provisioned with or imported into AWS Certificate Manager (ACM) in the same AWS Region where you'll create the Client VPN endpoint.
Go to "AWS Certificate Manager (ACM)" service, choose "Import certificate".
Import server and client certificates in turn.
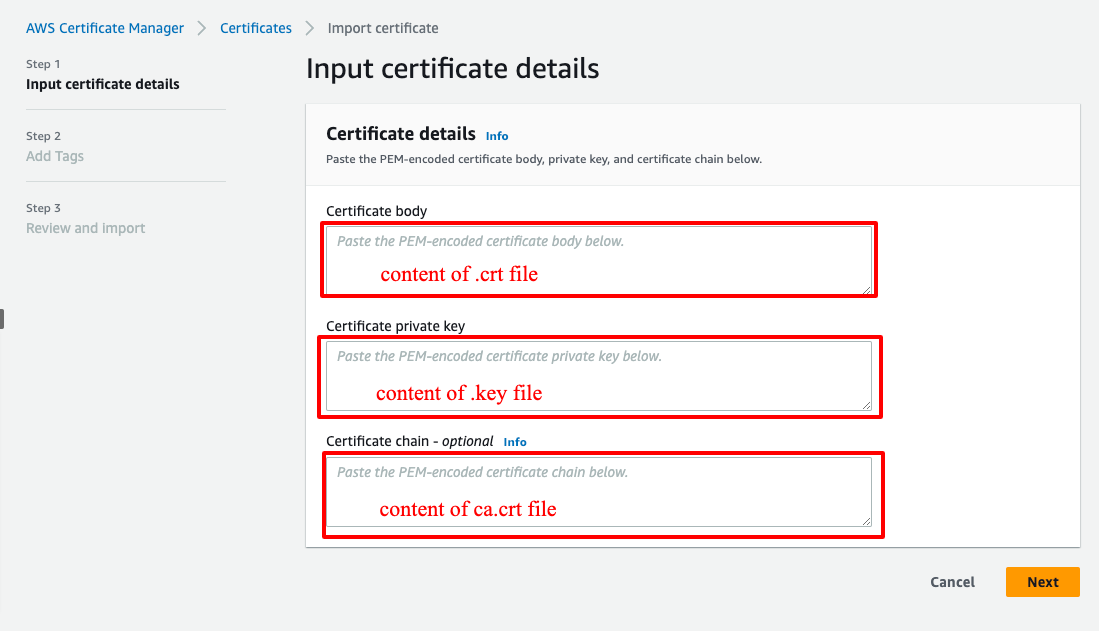 Step 2: Create Client VPN Endpoint
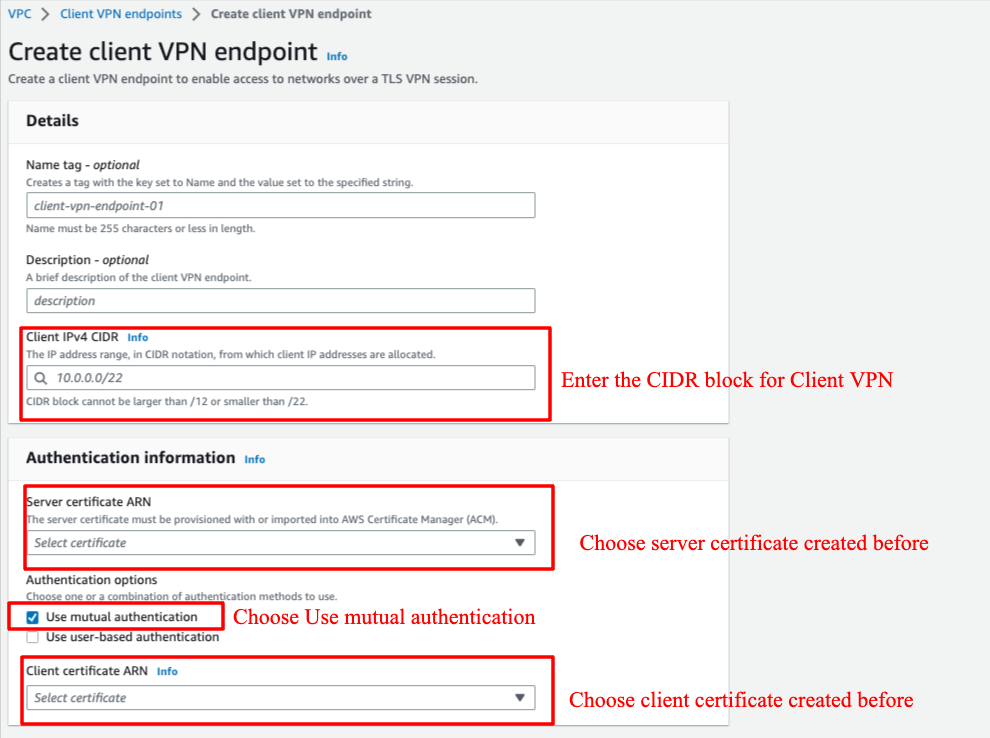
Go to "VPC", go to "Client VPN endpoints", choose "Create client VPN endpoint"
Step 2: Create Client VPN Endpoint
Go to "VPC", go to "Client VPN endpoints", choose "Create client VPN endpoint"
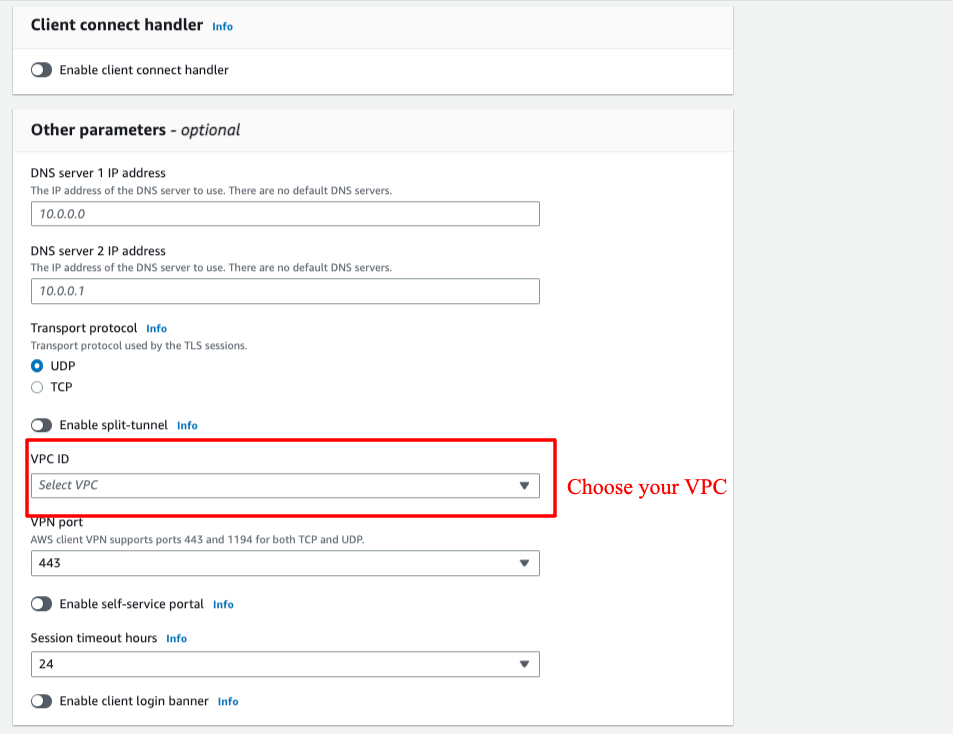 Step 3: Associate a target network
After Client VPN created, click to it, choose "Target network associations" tab, choose "Associate target network" button to select VPC and subnet.
Step 3: Associate a target network
After Client VPN created, click to it, choose "Target network associations" tab, choose "Associate target network" button to select VPC and subnet.
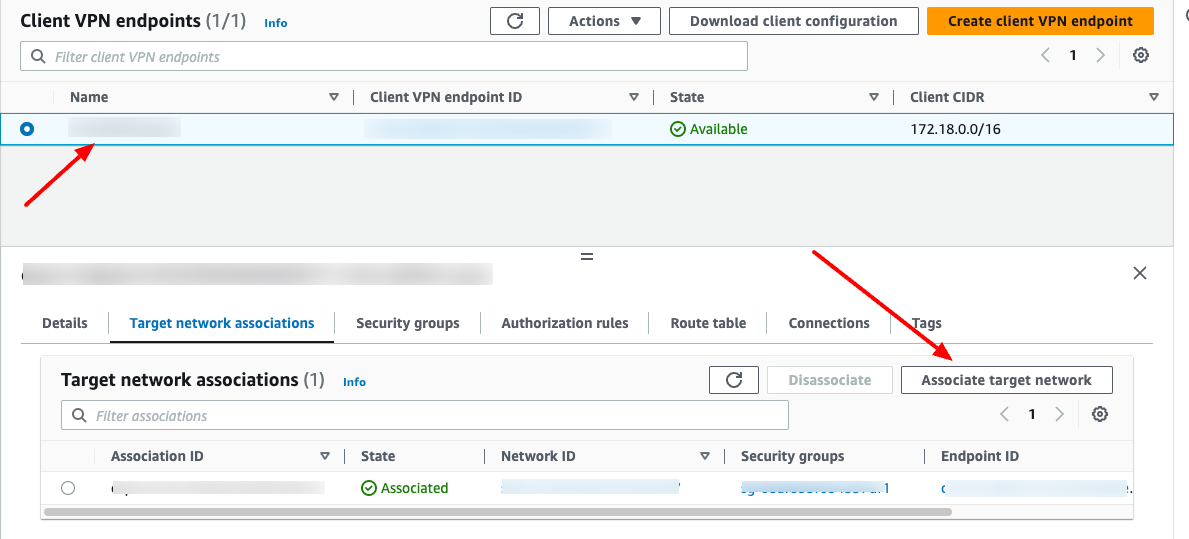 When you associate the first subnet with the Client VPN endpoint, the following happens:
The state of the Client VPN endpoint changes to available. Clients can now establish a VPN connection, but they cannot access any resources in the VPC until you add the authorization rules.
The local route of the VPC is automatically added to the Client VPN endpoint route table.
The VPC's default security group is automatically applied for the Client VPN endpoint.
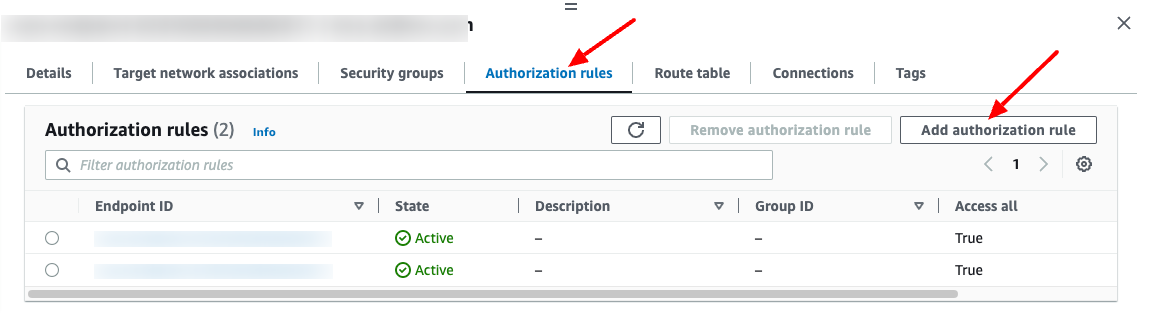
Step 4: Add an authorization rule for the VPC
Choose "Authorization rules" tab, choose "Add authorization rule" button and enter the CIDR of the network for which you want to allow access.
When you associate the first subnet with the Client VPN endpoint, the following happens:
The state of the Client VPN endpoint changes to available. Clients can now establish a VPN connection, but they cannot access any resources in the VPC until you add the authorization rules.
The local route of the VPC is automatically added to the Client VPN endpoint route table.
The VPC's default security group is automatically applied for the Client VPN endpoint.
Step 4: Add an authorization rule for the VPC
Choose "Authorization rules" tab, choose "Add authorization rule" button and enter the CIDR of the network for which you want to allow access.
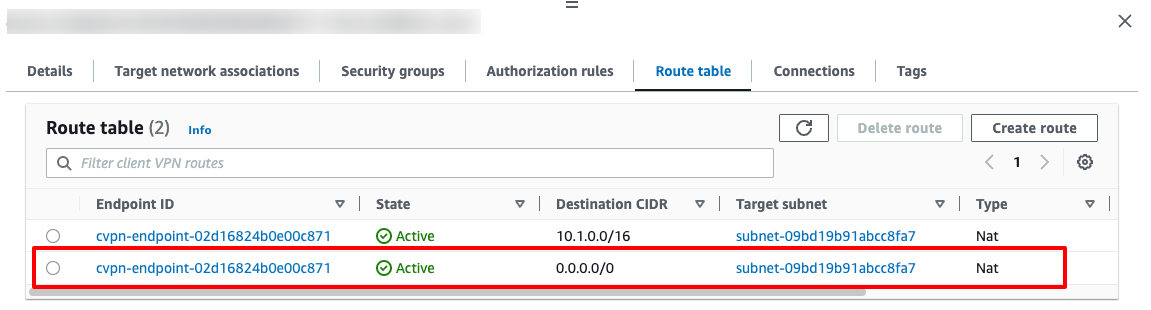
 Step 5: Provide access to the internet
Choose "Route Table", and then choose "Create Route".
For Route destination, enter 0.0.0.0/0. For Subnet ID for target network association, specify the ID of the subnet through which to route traffic.
For Destination network to enable access, enter 0.0.0.0/0, and choose Allow access to all users.
Step 5: Provide access to the internet
Choose "Route Table", and then choose "Create Route".
For Route destination, enter 0.0.0.0/0. For Subnet ID for target network association, specify the ID of the subnet through which to route traffic.
For Destination network to enable access, enter 0.0.0.0/0, and choose Allow access to all users.
 Step 6: Download configuration file
Step 6: Download configuration file
 Open the Client VPN endpoint configuration file using your preferred text editor. Add
Open the Client VPN endpoint configuration file using your preferred text editor. Add
 Step 2: Create Client VPN Endpoint
Go to "VPC", go to "Client VPN endpoints", choose "Create client VPN endpoint"
Step 2: Create Client VPN Endpoint
Go to "VPC", go to "Client VPN endpoints", choose "Create client VPN endpoint"

 Step 3: Associate a target network
After Client VPN created, click to it, choose "Target network associations" tab, choose "Associate target network" button to select VPC and subnet.
Step 3: Associate a target network
After Client VPN created, click to it, choose "Target network associations" tab, choose "Associate target network" button to select VPC and subnet.
 When you associate the first subnet with the Client VPN endpoint, the following happens:
The state of the Client VPN endpoint changes to available. Clients can now establish a VPN connection, but they cannot access any resources in the VPC until you add the authorization rules.
The local route of the VPC is automatically added to the Client VPN endpoint route table.
The VPC's default security group is automatically applied for the Client VPN endpoint.
Step 4: Add an authorization rule for the VPC
Choose "Authorization rules" tab, choose "Add authorization rule" button and enter the CIDR of the network for which you want to allow access.
When you associate the first subnet with the Client VPN endpoint, the following happens:
The state of the Client VPN endpoint changes to available. Clients can now establish a VPN connection, but they cannot access any resources in the VPC until you add the authorization rules.
The local route of the VPC is automatically added to the Client VPN endpoint route table.
The VPC's default security group is automatically applied for the Client VPN endpoint.
Step 4: Add an authorization rule for the VPC
Choose "Authorization rules" tab, choose "Add authorization rule" button and enter the CIDR of the network for which you want to allow access.
 Step 5: Provide access to the internet
Choose "Route Table", and then choose "Create Route".
For Route destination, enter 0.0.0.0/0. For Subnet ID for target network association, specify the ID of the subnet through which to route traffic.
For Destination network to enable access, enter 0.0.0.0/0, and choose Allow access to all users.
Step 5: Provide access to the internet
Choose "Route Table", and then choose "Create Route".
For Route destination, enter 0.0.0.0/0. For Subnet ID for target network association, specify the ID of the subnet through which to route traffic.
For Destination network to enable access, enter 0.0.0.0/0, and choose Allow access to all users.
 Step 6: Download configuration file
Step 6: Download configuration file
 Open the Client VPN endpoint configuration file using your preferred text editor. Add
Open the Client VPN endpoint configuration file using your preferred text editor. Add <cert></cert> and <key></key> tags to the file. Place the contents of the client certificate and the contents of the private key between the corresponding tags, as such: <cert>
Contents of client certificate (.crt) file
</cert>
<key>
Contents of private key (.key) file
</key> 6. Cited/Referenced Articles
7. About the proprietary solution "PrismScaler"
・PrismScaler is a web service that enables the construction of multi-cloud infrastructures such as AWS, Azure, and GCP in just three steps, without requiring development and operation.
・PrismScaler is a web service that enables multi-cloud infrastructure construction such as AWS, Azure, GCP, etc. in just 3 steps without development and operation.
・The solution is designed for a wide range of usage scenarios such as cloud infrastructure construction/cloud migration, cloud maintenance and operation, and cost optimization, and can easily realize more than several hundred high-quality general-purpose cloud infrastructures by appropriately combining IaaS and PaaS.
8. Contact us
This article provides useful introductory information free of charge. For consultation and inquiries, please contact "Definer Inc".
9. Regarding Definer
・Definer Inc. provides one-stop solutions from upstream to downstream of IT.
・We are committed to providing integrated support for advanced IT technologies such as AI and cloud IT infrastructure, from consulting to requirement definition/design development/implementation, and maintenance and operation.
・We are committed to providing integrated support for advanced IT technologies such as AI and cloud IT infrastructure, from consulting to requirement definition, design development, implementation, maintenance, and operation.
・PrismScaler is a high-quality, rapid, "auto-configuration," "auto-monitoring," "problem detection," and "configuration visualization" for multi-cloud/IT infrastructure such as AWS, Azure, and GCP.

