1. Introduction
Hello! We are a writer team from Definer Inc.
CI/CD (Continuous Integration/Continuous Deployment) implementation of Google Kubernetes Engine (GKE)'s safe container refers to the practice of automating the build, test, and deployment processes for containerized applications running on GKE. It involves setting up a pipeline that integrates code changes, builds container images, runs tests, and safely deploys them to the GKE cluster. The goal is to ensure a smooth and reliable software delivery process, promoting collaboration, agility, and quality assurance.
In this issue, you are wondering about the use of GKE's container CI/CD implementation.
Let's take a look at the actual screens and resources to explain in detail.
2. Purpose/Use Cases
The purpose of implementing CI/CD for GKE's safe container is to achieve the following objectives:
- Faster and Frequent Releases
- Consistent and Reliable Builds
- Automated Testing and Quality Assurance
- Improved Collaboration and Visibility
- Rollbacks and Easy Recovery
- Scalability and Flexibility
- Infrastructure as Code (IaC)
3. Setup
As a prerequisite, we assume that GKE and GitHub repositories exist.
First, we will set up Cloud Build and Container Registry.
(1) Connection with GitHub: To connect Cloud Build with your GitHub account, follow these steps:
- Navigate to the Cloud Build service in the Google Cloud Platform (GCP) console.
- Go to the "Triggers" section and select "Repository Management" or a similar option.
- Click on "Repository Connection" to establish a connection with your GitHub account.
- Provide the necessary authentication details, such as your GitHub username and password, or generate a personal access token to connect securely.
- Select the desired GitHub repository from your connected account.
This connection allows Cloud Build to access and retrieve source code from your GitHub repository for building and deploying containerized applications.
(2) Trigger settings: To configure triggers for Cloud Build, follow these steps:
- In the Cloud Build section, navigate to the "Triggers" or similar area.
- Click on "Create Trigger" to define a new trigger.
- Select the appropriate trigger event, such as "Push to branch", "Push new tag", or "Pull request". This determines when the trigger will be activated.
- Specify the source repository and branch that the trigger should monitor for changes.
- Configure the trigger settings, such as the build configuration file, build steps, and any additional build options.
The Cloud Build configuration file, usually named 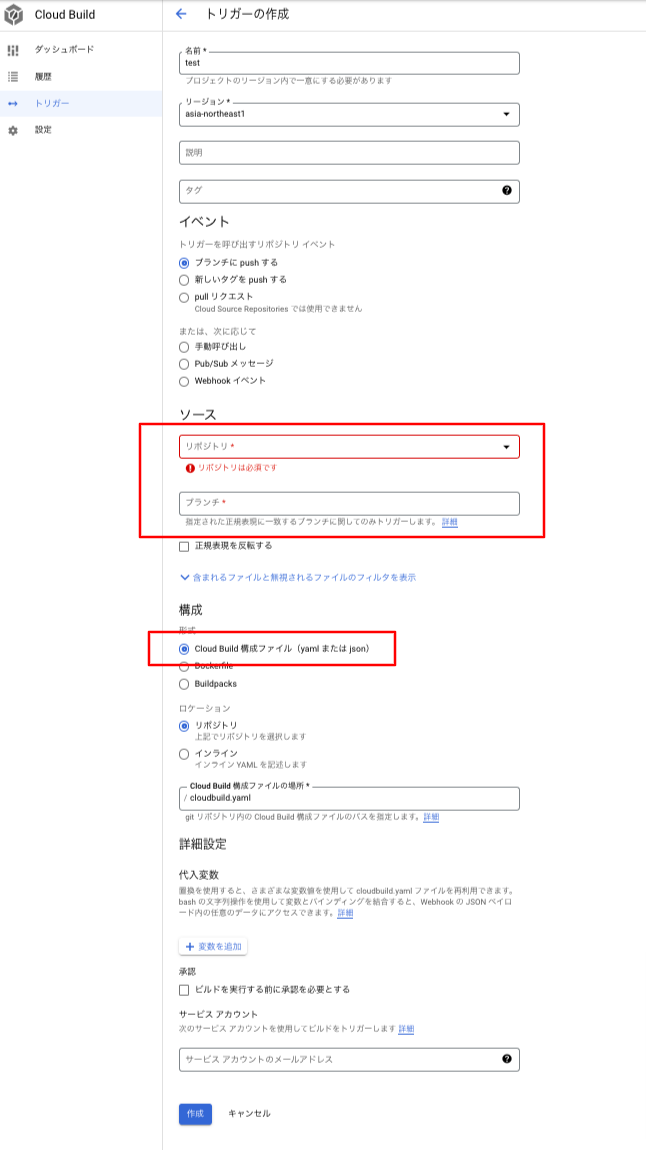 (3) Create Google Container Registry (GCR): To create a Google Container Registry, follow these steps:
- Access the "Google Container Registry" screen in the GCP console.
- Click on the option to create a new registry.
- Provide a unique name for your registry.
- Configure the desired access control and permissions settings for the registry, such as private or public access.
- Optionally, set up vulnerability scanning, image retention policies, and other registry-specific configurations.
- Confirm and create the Google Container Registry.
The Google Container Registry acts as a secure and managed container image registry, similar to other container registries like Docker Hub or AWS ECR. It allows you to store and manage your built container images for deployment.
(3) Create Google Container Registry (GCR): To create a Google Container Registry, follow these steps:
- Access the "Google Container Registry" screen in the GCP console.
- Click on the option to create a new registry.
- Provide a unique name for your registry.
- Configure the desired access control and permissions settings for the registry, such as private or public access.
- Optionally, set up vulnerability scanning, image retention policies, and other registry-specific configurations.
- Confirm and create the Google Container Registry.
The Google Container Registry acts as a secure and managed container image registry, similar to other container registries like Docker Hub or AWS ECR. It allows you to store and manage your built container images for deployment.
cloudbuild.yaml, contains the instructions and steps for building and deploying your containerized application. It defines the build steps, dependencies, and environment settings required for the build process.
 (3) Create Google Container Registry (GCR): To create a Google Container Registry, follow these steps:
- Access the "Google Container Registry" screen in the GCP console.
- Click on the option to create a new registry.
- Provide a unique name for your registry.
- Configure the desired access control and permissions settings for the registry, such as private or public access.
- Optionally, set up vulnerability scanning, image retention policies, and other registry-specific configurations.
- Confirm and create the Google Container Registry.
The Google Container Registry acts as a secure and managed container image registry, similar to other container registries like Docker Hub or AWS ECR. It allows you to store and manage your built container images for deployment.
(3) Create Google Container Registry (GCR): To create a Google Container Registry, follow these steps:
- Access the "Google Container Registry" screen in the GCP console.
- Click on the option to create a new registry.
- Provide a unique name for your registry.
- Configure the desired access control and permissions settings for the registry, such as private or public access.
- Optionally, set up vulnerability scanning, image retention policies, and other registry-specific configurations.
- Confirm and create the Google Container Registry.
The Google Container Registry acts as a secure and managed container image registry, similar to other container registries like Docker Hub or AWS ECR. It allows you to store and manage your built container images for deployment. 4. Building CI/CD pipeline with Cloud Build
Next, we will set up CI/CD for Cloud Build.
(1) Build settings: In the Cloud Build configuration file (
cloudbuild.yaml), you will define the build settings and steps required for your CI/CD pipeline. These settings include the instructions for building your containerized application, running tests, and packaging the application for deployment.
Typically, the cloudbuild.yaml file will include:
- Build steps: These are the individual tasks and commands that are executed during the build process. For example, you may have build steps to install dependencies, compile code, run tests, and create the container image.
- Build triggers: You can define triggers in the cloudbuild.yaml file that specify when the build process should be triggered. Triggers can be based on events like code changes, branch updates, or manual triggers. steps:
- name: 'node:11.10.0'
id: 'Install'
args: ['npm', 'install']
dir: 'test-api'
- name: 'node:11.10.0'
id: 'Build'
args: ['npm', 'run', 'staging-build']
dir: 'test-api'
- name: 'gcr.io/cloud-builders/docker'
id: 'Build Image'
args: ['build', '-t', '${GCR Registry ID}', '.', '-f', 'Dockerfile']
dir: 'test-api'
- name: 'gcr.io/cloud-builders/docker'
id: 'PushR'
args: ['push', '${GCR Registry ID}']
dir: 'test-api' (2) Specifying the GCR image in GKE: To specify the Google Container Registry (GCR) image in the manifest file used in Google Kubernetes Engine (GKE), follow these steps:
- Open the manifest file that defines your Kubernetes deployment, such as a YAML file.
- Update the
image field in the manifest file to reference the container image stored in GCR. The image reference should follow the format <GCR_REGISTRY_HOST>/<PROJECT_ID>/<IMAGE_NAME>:<TAG>.- Replace
<GCR_REGISTRY_HOST> with the appropriate GCR registry URL, <PROJECT_ID> with your Google Cloud project ID, <IMAGE_NAME> with the name of your container image, and <TAG> with the specific version or tag of the image.By specifying the GCR image in the GKE manifest file, you ensure that the correct container image is used for deployment in your Kubernetes cluster.
(3) Deployment settings: In the
cloudbuild.yaml file, you will also define the deployment settings, which specify how your application is deployed to GKE. These settings typically include:- Deployment strategy: Specify the deployment strategy, such as rolling update, blue/green deployment, or canary release.
- Kubernetes manifests: Provide the Kubernetes manifests (YAML files) that describe the desired state of your application in GKE. This includes deployment configurations, services, volumes, and other resources.
- Deployment steps: Define the deployment steps in the
cloudbuild.yaml file, such as applying the Kubernetes manifests, rolling out the new version, and performing health checks. steps:
- name: 'gcr.io/cloud-builders/kubectl'
id: 'Deploy'
args: ['apply', '-f', '${manifest file path}']
env:
- 'CLOUDSDK_COMPUTE_ZONE=asia-northeast1-a'
- 'CLOUDSDK_CONTAINER_CLUSTER=gcp-test-sandbox'
dir: 'test-api' 5. Cited/Referenced Articles
6. About the proprietary solution "PrismScaler"
・PrismScaler is a web service that enables the construction of multi-cloud infrastructures such as AWS, Azure, and GCP in just three steps, without requiring development and operation.
・PrismScaler is a web service that enables multi-cloud infrastructure construction such as AWS, Azure, GCP, etc. in just 3 steps without development and operation.
・The solution is designed for a wide range of usage scenarios such as cloud infrastructure construction/cloud migration, cloud maintenance and operation, and cost optimization, and can easily realize more than several hundred high-quality general-purpose cloud infrastructures by appropriately combining IaaS and PaaS.
7. Contact us
This article provides useful introductory information free of charge. For consultation and inquiries, please contact "Definer Inc".
8. Regarding Definer
・Definer Inc. provides one-stop solutions from upstream to downstream of IT.
・We are committed to providing integrated support for advanced IT technologies such as AI and cloud IT infrastructure, from consulting to requirement definition/design development/implementation, and maintenance and operation.
・We are committed to providing integrated support for advanced IT technologies such as AI and cloud IT infrastructure, from consulting to requirement definition, design development, implementation, maintenance, and operation.
・PrismScaler is a high-quality, rapid, "auto-configuration," "auto-monitoring," "problem detection," and "configuration visualization" for multi-cloud/IT infrastructure such as AWS, Azure, and GCP.

